Protecting your personal data
by Jani on Jan 14th, 2023One of the key responsibilities for any software-as-a-service vendor is to maintain the privacy and confidentiality of the pieces of information collected about your customers. This information, or personal data as it is typically called, must be stored, processed and accessed in a manner that ensures that no 3rd party can gain unauthorized access to the data.
I will describe in this blog post some of the key aspects of how we have chosen to protect your personal data here at PhotoVaultOne, as well as some of the key technical concepts we have applied to largely eliminate certain common privacy impacting concerns for web applications.
Limiting the data that is collected
At PhotoVaultOne, we follow the principle of collecting the least amount of data about our customer as possible. We have chosen to follow this principle because the best way to protect your data is to not collect it in the first place.
We collect only the minimum basic information needed to contact you (email address and name). For example, your login information (including password) is stored only with Google, and we have no access to this information. Also, your billing information such as credit card information and location information relevant for taxation purposes is collected only by our billing partner Stripe, and not stored in our system at all.
Protecting your data at rest
Similar to how we store your library content end-to-end encrypted, information about you is stored encrypted in our databases.
The industry standard for database encryption is to encrypt the database volume. This offers a good security baseline. We have however decided to go beyond this, and set the bar higher on what in our oppinion should be the norm for data protection.
At PhotoVaultOne, in addition to database volume encryption, your personal data is additionally encrypted client-side in our application before it is transmitted and written to the database. This added protection makes it significantly harder for any 3rd party to read your data, even if they would have access to it.
When your personal data is stored client-side encrypted in our database, attempting to read it outside of our application will not succeed. Instead, you will get a blob of binary data which you cannot process. Below is an actual screenshot of how this looks like from a development instance (not real user data):
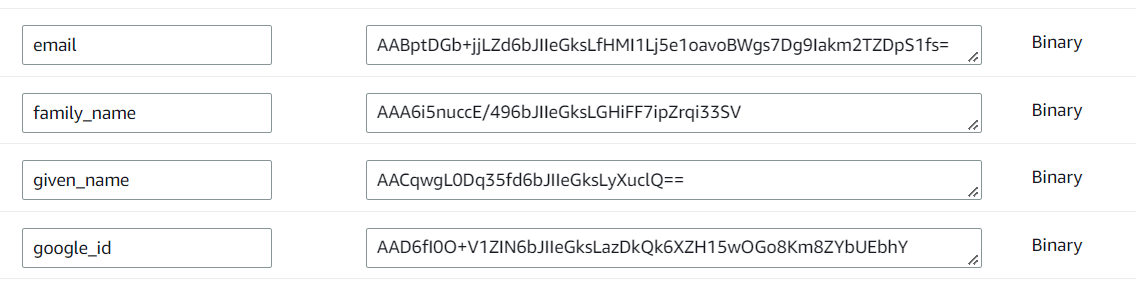
Isolation of user processing in application
Traditionally multi-tenant applications have been built with a single set of access credentials that are utilized to access the data for all users in the service. For us at PhotoVaultOne, this was not good enough. If the application can access any users data at any time, programming errors in the application can cause issues with data isolation between users, and even expose other users data in the worst case.
To protect against such errors, PhotoVaultOne has been implemented using a modern access control mechanism called "attribute-based access control", or ABAC for short. By utilizing ABAC, our application always executes with scoped permissions that allow the application to access only the data belonging to the user who initiated the request. This significantly reduces the impact for a wide range of potential errors in our application logic, by simply not allowing the application to access data for multiple users within the execution of a single request.
Summary
I have explained how at PhotoVaultOne we apply multiple layers of both logical and technical protection for your personal data. We believe this should be the bar for all SaaS vendors, and anything less would not do.
You can read more about the technical protections from an AWS Security blog post that I recently wrote, which describes how ABAC and client-side encryption can be used together for additional protection of personal data - exactly as we do here at PhotoVaultOne.
About the author
Jani is the Founder and Chief Architect of PhotoVaultOne. Jani is also a Principal Solutions Architect at Amazon Web Services, where he strives to be a trusted advisor for Enterprises in the Nordics.
Disclaimer: All opinions and claims expressed are personal, and not that of Amazon Web Services.